Examen Corrigé En Réseaux Informatiques QCM
Exercice 1 : (10 pts) - Choisir la bonne réponse - QCM -(2 pts pour chaque réponse)
Q1 : Quelle partie d’un réseau fournit des applications et des données aux ordinateurs hôtes
Q2 : A quoi sert une carte réseau ?
Q3 : Que connectent les routeurs ?
Q4 : A quoi sert un répéteur ?
Q5 : Pour créer un réseau local simple de quatre ordinateurs, vous utiliseriez un(e) ______________ pour les raccorder.
Partie Pratique : (20 pts)
Q1 : Quelle partie d’un réseau fournit des applications et des données aux ordinateurs hôtes
a) Serveur
b) Concentrateur
c) Routeur
d) Pont
a) Établie, gère et ferme les sessions entre des applications, et gère l’échange de données entre les entités de la couche présentation.
b) Donne à l’hôte accès au média.
c) Fournit des services aux processus d’applications
a) Les ponts et les répéteurs
b) Les ponts et les concentrateurs
c) Deux réseaux ou plus
d) Les concentrateurs et les nœuds
a) Connecter un réseau local à un réseau long distance
b) Amplifier et resynchroniser les signaux réseau
c) Enregistrer des pages Web et les répéter pour d’autres utilisateurs
d) Transmettre les signaux horaires entre des unités réseau
a) Câble d’interconnexion
b) Ligne série
c) Concentrateur
d) Routeur
Q6 : Si quatre hôtes sont connectés à un concentrateur, puis à Internet, combien faut-il d’adresses IP pour ces cinq unités ?
a) Un
b) Deux
c) Quatre
d) Cinq
Q7 : Les unités d’interconnexions de réseaux sont utilisés pour relier des ?
a) Réseaux locaux à d’autres réseaux locaux
b) Réseaux locaux à des réseaux longue distance
c) Réseau longue distance à d’autres réseaux longue distance
d) Toutes ces réponses
Q8 : Identifiez un avantage de l’utilisation de la fibre optique dans les réseaux.
a) Peu coûteux
b) Facile à installer
c) Insensible aux interférences électromagnétiques
d) Disponible avec ou sans blindage extérieur
Q9 : Quel énoncé décrit le mieux la topologie de bus ?
a) Tous les nœuds directement connectés à un point central tel qu’un concentrateur.
b) Tous les nœuds sont directement connectés à une liaison physique.
c) Tous les nœuds sont connectés à exactement deux autres nœuds.
Q10 : Quelle définition parmi les suivantes décrit le mieux une topologie en étoile ?
a) Topologie de réseau local selon laquelle un nœud central est connecté par câblage à d’autres nœuds qui en rayonnent.
b) Topologies de réseau local selon laquelle les transmissions de stations réseau se propagent sur la longueur d’un câble coaxial unique.
c) Topologie de réseau local qui utilise un nœud de circuit duquel partent les branches vers d’autres nœuds.
d) Topologie de réseau local
Exercice 1 : (10 pts)
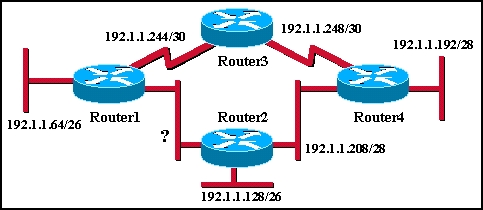
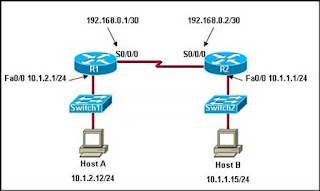
1) A quoi correspond ce schéma ? Expliquez le mode de fonctionnement.
2) Remplir le tableau suivant : (6 pts)
Adresse IP | Classe | Identificateur de Réseau | Identificateur d’hôte | Masque de sous réseau par défaut |
12.3.2.1 | ||||
220.30.2.5 | ||||
56.9.6.4 |
3) Donner une commande pour tester la connexion entre deux ordinateurs. (2 pts)
4) Donner une commande pour afficher la configuration réseau d’un ordinateur. (2 pts)
-------------------------------------------------------------------------------------------------
La Correction de l'examen